Introduction
With each day, the forms of cyber-attacks rise. To trick people and steal their money, fraudsters are using newer techniques. Sniffing is one of the simplest hacking methods. The fraudsters use the method of tracking and collecting all the data packets that move through a computer network using packet sniffers in this form of attack. Packet Sniffers are used to keeping track of data traffic going through their network by network operators. In this article, we will discuss sniffing, sniffing attack, sniffing tools and, the difference between spoofing and phishing.
What is sniffing?
“sniffing” refers to the real-time detection of internet traffic. Sniffers are applications or hardware gadgets that can spy on you and all your actions on the internet. Sniffers will sometimes be legal, sometimes illegal, and leave you feeling vulnerable. To learn what sniffers are, how they function, and how to defend yourself from hacker sniffing attacks, read on. Sniffing is the method of tracking and collecting all data packets that are used by packet sniffers to travel through a computer network. Packet Sniffers are used to keeping track of data traffic passing through their network by network administrators. These are called analyzers for network protocols. Similarly, the use of these packet sniffing techniques to intercept data packets on a network is used by malicious attackers.
To retrieve and steal confidential information such as passwords, usernames, credit card information, etc., data packets collected from a network are used. In the form of software or hardware, attackers insert these sniffers into the device.
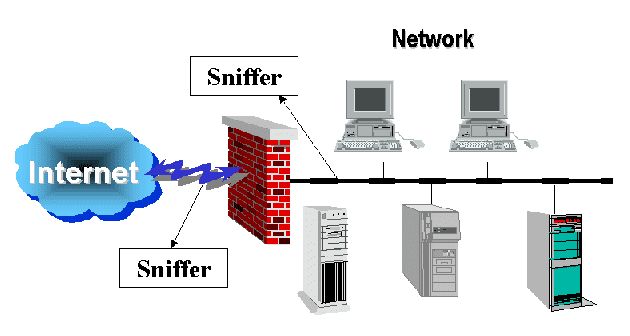
What is a Sniffing attack?
To hear the calls that a person gets to get some information, remember back in some movies, police agencies, and criminals used to bug the phone lines. This is a prime example of assault sniffing. This method may be used to inspect the telephone lines and assess the call quality, but it was used by criminals for their own illegitimate purpose. Sniffing can be done using an application, hardware devices at the network and host level in the internet world. The attackers can intercept and read any network packet that has information in plain text. Usernames, passwords, secret codes, banking data, or any information that is of importance to the intruder may be that information. The only technological equivalent of a physical spy is this assault.
Sniffing tools
There are so many sniffing tools available over a network, and they all have their own characteristics to help a hacker analyze traffic and dissect the data. Highly popular applications are sniffing devices. Some that are mentioned here,
- BetterCAP is a powerful, versatile, and portable tool created to carry out various types of network MITM attacks, manipulate real-time HTTP, HTTPS, and TCP traffic, sniff for credentials, and much more.
- Ettercap-Ettercap is an extensive man-in-the-middle assault package. It features live link sniffing, on-the-fly filtering of content, and many other fascinating tricks. Active and passive dissection of several protocols is provided, and many networks and host analysis features are included.
- Wireshark-It is one of the packet sniffers most commonly known and used. It contains an immense range of features designed to assist in traffic dissection and analysis.
- Tcpdump-It is a well-known packet analyzer command-line. It offers the opportunity during transmission over the network to intercept and observe TCP/IP and other packets.
- WinDump − A Windows port of the popular tcpdump Linux packet sniffer, which is the perfect command-line tool for displaying header information.
- OmniPeek − Manufactured by WildPackets, OmniPeek is a consumer product that is the evolution of the product EtherPeek.
What is the difference between spoofing and phishing?
Spoofing: Spoofing is a type of computer system attack in which the attacker attempts to steal the legitimate user’s identity and behave as another human. This kind of attack is carried out to break the system’s security or to steal users’ data. For instance,
Normally, hackers alter their IP addresses to hack a website so that it is not possible to locate the hacker. Any malicious software needs to be downloaded to the victim’s device.
Phishing: Phishing is a type of computer device attack where the intruder attempts to locate users’ sensitive information utilizing electronic communication deceptively by intending to automatically be from a similar trusted organization. For instance,
Hackers often ask for OTP or hidden PIN of the bank transaction via contact by acting as a bank employee, which is a form of fraud. It doesn’t need such malicious software.
In the context of TCP/IP protocol suites, the cybersecurity course discusses real-time cybersecurity strategies and methods. Learners would be exposed to the methods used for designing and configuring firewall technologies such as packet filters and proxies to protect business properties. In typical enterprise settings, perimeter solutions such as firewalls and intrusion prevention systems have shown to have major disadvantages. As advanced persistent threats from nation-state actors, the result of such weakness is seen to occur still. It has been shown that such attacks and DDOS and third-party attacks have possible solutions for modern business.
Conclusion
Sniffers keep an eye on your web traffic in real-time, making them potentially very invasive, like websites you visit and everything you download or upload. Yet, various types of sniffers do exist. ‘Sniffer’ with a capital S refers to NetScout’s trademarked tool, which enables network administrators to control bandwidth and ensure that no single user takes up too much of the available space. With a lowercase s, “sniffer” applies to both other forms of benign and malignant packet sniffers. To retain the smooth flow of traffic through a network, most legal sniffers are used.
References:
https://www.smarthaus.com.ar/index.php/9-noticias/11-how-to-protect-from-packet-sniffers
https://www.digitalinformationworld.com/2019/04/how-to-protect-yourself-from-packet-sniffing.html